Originally posted by NickFitz
View Post
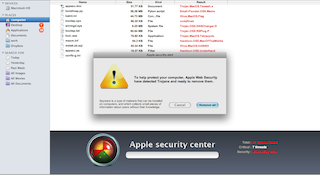
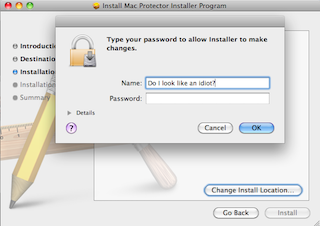
This time it was a product called MacKeeper, which looks extremely dodgy. Dodgy looking Russian(ish) names too. There are reports on
Most disturbingly it greyed out nearly all Safari's menu options, but Quit was still there, and that's what I used.
*url scrubbed because clicking on links to reviews on that site initiate a download.
P.S. There's a glowing write up of it at applenerd.net, but I have to assume that's fake as well. Ooh yes it is - the Facebook bit on the RHS is just an image that does nowt.
P.P.S. It's time Google got their act together on this one.


 to the bell end that neg repped me for this thread and didn't sign it
to the bell end that neg repped me for this thread and didn't sign it 








Leave a comment: